Application Programming Interfaces (APIs) are gateways for enabling secure communication between software systems. They refine operations, connect ecosystems, and drive innovation in a data-centric world. However, as a vital part of the process, APIs are leading targets for cyber threats. The State of API Security Report Q1 2023 surveyed over 1,600 respondents, 60% of whom reported that an API-related data breach had occurred in the last two years. Of the same, 74% had at least 3 API-related data breaches, 40% had five or more, and 11% faced over seven. From broken object-level authorisation to injection attacks, APIs expose sensitive data and core functionalities to potential exploitation.
The challenge lies in keeping APIs open for business innovation while closing them off to malicious actors. This guide provides actionable insights, real-world examples, and lifecycle-oriented strategies to help Australian organisations secure their APIs to reduce risk and maintain a strong defence posture.
API-related data breaches from 2021-23
1,629 respondents were surveyed across 100 countries and over 6 major industries.
Source: State of API Security Report Q1 2023
Why API Security Matters
API security is also necessary, as APIs are integral to modern digital systems. Without proper security measures, vulnerabilities such as broken authorisation, injection attacks, and rate-limiting failures can lead to data breaches and service disruptions. High-profile incidents, like the Optus breach, demonstrate how unauthenticated API endpoints can expose millions of personal records, underlining the importance of strengthened security practices.
As APIs become essential for machine-to-machine communication and AI-driven applications, their attack surfaces grow, making them prime targets for bot-driven abuse and unauthorised access. Securing APIs with stringent authentication protocols, rate limiting, and continuous monitoring ensures the integrity of digital ecosystems and protects businesses from financial loss, compliance violations, and operational downtime.
Why Is API Security So Important?
APIs are necessary for modern digital services as gateways to sensitive data and critical operations. This pivotal role has also made them a prime target for cybercriminals. High-profile breaches such as the Optus leak in 2022 and the Facebook API breach in 2019 highlight the devastating impact of API vulnerabilities, from data exfiltration to service disruptions to an entire nation.
Recognising these risks, Gartner incorporated API security into its 2022 security reference architecture, advocating for specialised tools and strategies to combat API-specific threats. Securing APIs is no longer optional; it is essential for protecting sensitive data, maintaining operational resilience, and upholding trust with customers.
Understanding API Security
Modern APIs differ significantly from traditional web applications regarding attack surfaces, protocols, and protection measures. While traditional applications often have fewer well-defined entry points, APIs resemble a castle with many openings—each API endpoint is a potential door through which attackers can exploit vulnerabilities.
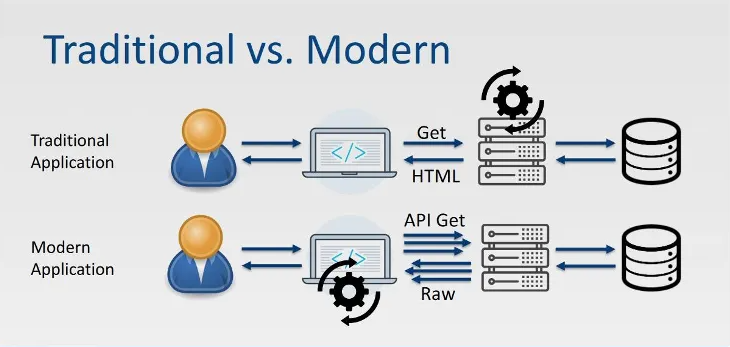
Source: OWASP
Understanding APIs is crucial for safeguarding your business. Unlike traditional applications that rely on static, browser-based protocols, APIs leverage dynamic and evolving formats such as REST, SOAP, and GraphQL. These variations demand tailored security solutions to address the unique risks posed by each protocol. For example, REST APIs rely on secure HTTP methods, while GraphQL presents distinct challenges due to its flexible querying structure.
Protecting APIs thus requires a layered approach, combining broadened access controls, rate limiting, and continuous monitoring. By addressing APIs’ complexity with strategies suited to their dynamic nature, organisations can guard against the diverse threats targeting these critical systems.
Understanding API Types
APIs come in various types, each with unique structures, use cases, and security considerations. Beyond REST and SOAP, modern architectures also commonly use gRPC and GraphQL, which bring distinct advantages and challenges. Understanding these options helps organisations select the best API for their needs while addressing specific security risks.
- REST (Representational State Transfer): A lightweight architectural style that uses standard HTTP methods (GET, POST, PUT, DELETE) and flexible data formats like JSON or XML. REST APIs are popular for their simplicity and scalability but require robust rate limiting and input validation to prevent abuse and injection attacks.
- SOAP (Simple Object Access Protocol): A protocol-based approach reliant on XML for highly standardised and secure communication, making it ideal for enterprise systems. Its strict standards come with added complexity but include built-in error handling and WS-Security for robust security.
- gRPC (gRPC Remote Procedure Call): A high-performance framework that uses Protocol Buffers (Protobuf) for serialisation and supports bi-directional streaming. gRPC is widely used in microservices for its speed and efficiency but requires careful management of TLS encryption and authentication mechanisms to secure communication.
- GraphQL: A query language allowing clients to request specific data from an API, enhancing efficiency and flexibility. However, its flexible querying structure introduces risks like data over-fetching and abuse through costly or nested queries. Security measures such as query complexity analysis and rate limiting are essential to prevent misuse.
What’s The Difference Between REST and SOAP?
SOAP is a rigid XML protocol for standardised communication that is ideal for enterprise systems. REST is an architectural style using lightweight HTTP methods with flexible formats, perfect for scalability and rapid development of web and mobile apps. REST is simpler; SOAP is more secure.
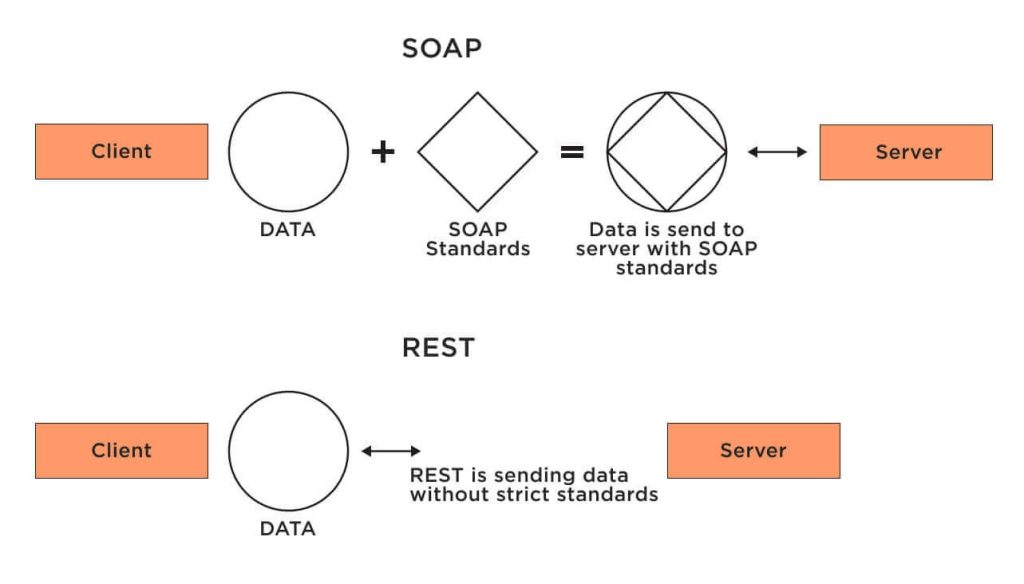
Source: Jelvix
Understanding these differences is essential for choosing the right protocol based on your organisation’s requirements, ensuring that the chosen API architecture aligns with functional and security needs.
Security Considerations
- REST and GraphQL: Require robust input validation and rate limiting to manage abuse from client-side requests
- SOAP and gRPC: Depend heavily on encryption (e.g., TLS) and strong authentication to protect sensitive data in highly standardised or high-performance environments
- GraphQL-Specific: Employ maximum query depth and complexity thresholds to prevent resource exhaustion and protect backend systems from abuse
Choosing the right API type depends on your organisation’s goals, be they scalability, security, or performance. Aligning those needs with appropriate security strategies ensures API integrity and resilience.

The API Security Lifecycle
Organisations must adopt a lifecycle approach encompassing design, development, testing, staging, and production to secure APIs. Collaboration between developers, security engineers, and operations teams is required at each stage to ensure the integration of security measures and a proactive response to emerging threats.
1. Design: Secure APIs from the Start
The principle of least privilege ensures minimal access permissions, reducing potential attack surfaces. Robust authentication protocols like OAuth 2.0 and OpenID Connect strengthen user verification, while strict schema validation prevents injection attacks by validating inputs.
Developers and security teams should collaborate to define access roles and validation rules early in the API design phase, ensuring security is embedded from the start.
2. Development: Build with Security Embedded
Incorporating OWASP’s Top 10 protections against vulnerabilities like broken authentication and excessive data exposure is crucial for API security. Implementing shift-left practices, such as conducting Static Application Security Testing (SAST) early, helps identify issues before deployment. Strong encryption standards safeguard sensitive data during transit and storage.
Collaboration between developers and security engineers ensures automated security testing is embedded into CI/CD pipelines, while secure coding practices enhance overall resilience.
3. Testing: Continuous Security Integration
Dynamic and fuzz testing using tools like Postman and JMeter simulate malicious inputs and identify runtime vulnerabilities. Integrating automated security checks into CI/CD pipelines with tools like Jenkins or GitHub Actions and testing APIs in staging environments ensures early issue detection.
Collaboration between operations teams and developers is essential to simulate realistic API usage and verify system resilience under load.
4. Production and Maintenance: Monitor and Adapt
API gateways enforce policies like rate limiting and access control while monitoring tools (such as SIEM systems) detect and respond to real-time threats. Regularly deprecating outdated APIs and introducing secure updates reduce vulnerabilities.
Continuous collaboration between operations and security teams ensures proactive monitoring and quick responses to emerging risks.

What Are The API Security Best Practices?
The OWASP API Security Top 10 – 2023 remains a vital framework for developers and security engineers. It outlines the most critical security risks associated with APIs. Here’s a comprehensive list:
- Broken Object Level Authorisation: APIs often expose endpoints that handle object identifiers, creating a broad attack surface for object-level access control issues. Every function accessing a data source using user input should implement object-level authorisation checks.
- Broken Authentication: Incorrect implementation of authentication mechanisms can allow attackers to compromise authentication tokens or exploit flaws to impersonate other users, undermining API security.
- Broken Object Property Level Authorisation: This issue arises from the lack of or improper authorisation validation at the object property level, leading to unauthorised information exposure or manipulation.
- Unrestricted Resource Consumption: APIs require network bandwidth, CPU, memory, and storage. Unrestricted consumption can lead to Denial of Service attacks or increased operational costs.
- Broken Function Level Authorisation: Complex access control policies and unclear separation between administrative and regular functions can lead to authorisation flaws, allowing attackers to access unauthorised resources or functions.
- Unrestricted Access to Sensitive Business Flows: APIs that expose business flows without considering how excessive automated use can harm the business are vulnerable, even without implementation bugs.
- Server Side Request Forgery (SSRF): Occurs when an API fetches a remote resource without validating user-supplied URIs, enabling attackers to send crafted requests to unintended destinations.
- Security Misconfiguration: Complex API configurations can lead to security vulnerabilities if not properly managed, opening the door to various attacks.
- Improper Inventory Management: Lack of proper documentation and inventory of APIs can lead to issues like deprecated API versions and exposed debug endpoints, increasing security risks.
- Unsafe Consumption of APIs: Trusting data from third-party APIs without proper validation can introduce vulnerabilities, as attackers may target integrated services to compromise the main API.
For a detailed understanding and mitigation strategies for each risk, refer to the official OWASP API Security Top 10 – 2023 documentation.
Updated Insights on OWASP API Security Top 10
The OWASP API Security Top 10 has updates aligned with emerging threats in API security, particularly in cloud-based architectures. Recent updates include:
- API8 – Injection Vulnerabilities: Expanded to cover NoSQL injection risks
- API10 – Insufficient Logging and Monitoring: Reinforces real-time activity tracking needs
Mitigating Emerging Threats
Addressing these risks requires a combination of preventive measures and adaptive strategies:
- Encrypted Communication: Secure data transmission between APIs using TLS to mitigate interception risks
- Comprehensive Access Controls: Implement OAuth scopes, rate limiting, and object-level authorisation to minimise unauthorised access
- Continuous Monitoring and Bot Detection: Use tools like Web Application Firewalls (WAFs), behavioural analytics, and AI-based systems to identify unusual patterns indicative of bot activity or targeted abuse
- AI-Specific Security Measures: Limit API access to sensitive AI endpoints and monitor model usage for unusual behaviour
By integrating these defences, organisations can safeguard their APIs against traditional risks and emerging threats in the era of automated and AI-driven technologies.
A Checklist for API Security
Organisations should adopt a systematic approach integrating preventative, detective, and responsive measures to ensure comprehensive API security. The following checklist outlines critical steps to secure APIs effectively:
- Implement Authentication Standards: Use OAuth or API keys.
- Monitor and Log Activity: Track API usage and detect anomalies.
- Rate Limiting: Prevent DoS attacks and excessive resource usage.
- Encrypt Data: Secure both in-transit and at-rest information.
- Use API Gateways: Enforce traffic controls and centralise security policies.
What Are Some Practical Tools for API Security?
Securing APIs requires specialised tools to protect against vulnerabilities, monitor traffic, and respond to threats in real-time. These tools address API security and enhance testing and monitoring capabilities. Below are the top API Security Tools categorised for API security and testing:
API Security Tools
- Salt Security: Provides real-time threat detection and prevention by analysing API traffic and identifying vulnerabilities like BOLA or injection attacks
- NoName Security: Delivers full visibility into API security posture, including automated threat detection and remediation
- Kong Gateway: A high-performance API gateway that secures APIs through authentication, rate limiting, and traffic control policies
- Traceable AI: Tracks API activity end-to-end, enabling comprehensive visibility into potential threats and anomalies to prevent data breaches
API Testing Tools
- Postman: Streamlines functional and security testing, enabling developers to validate API requests and integrate testing into CI/CD pipelines
- SoapUI: Provides advanced testing configurations for SOAP and REST APIs, supporting comprehensive functional and load testing
- Fiddler: Monitors HTTP requests, identifies anomalies, and simulates attack vectors to help developers test for potential vulnerabilities
Key API Security Risks
APIs come with unique vulnerabilities that attackers can exploit if left unchecked. Common risks include unauthorised access, malicious commands, and unregulated traffic, which can compromise sensitive data or disrupt services. Strong security measures like encryption, access controls, and real-time monitoring can mitigate threats and safeguard API integrity.
Key API Security Risks:
- Broken Object-Level Authorisation (BOLA): Attackers exploit weak access controls to manipulate API endpoints, gaining unauthorised access to sensitive data. As APIs handle more granular permissions, maintaining robust object-level authorisation becomes critical to avoid data breaches.
- Injection Attacks: Malicious commands, such as SQL or XML injections, are inserted into API inputs to compromise servers, expose sensitive information, or execute unauthorised actions. APIs handling machine-generated queries must implement strict input validation to prevent such exploits.
- Rate Limiting Issues: Insufficient request throttling can allow malicious actors to overwhelm API endpoints, causing Denial-of-Service (DoS) attacks or resource depletion. Bot-driven abuse exacerbates this threat as automated systems send high volumes of requests to disrupt services or scrape data.
- API Abuse by Bots: Automated scripts can exploit APIs for tasks such as credential stuffing, data scraping, or unauthorised access. Advanced bot detection techniques, such as behavioural analytics and machine learning-based anomaly detection, are essential to identify and block malicious activity.
- AI-Driven Exploitation: APIs connected to AI systems face unique risks, such as manipulating machine-learning models or exploiting prediction endpoints. Securing APIs in this context requires encryption, robust authentication, and limiting endpoint exposure to prevent AI system abuse.

Real-World Examples of API Breaches
Facebook API Breach (2019)
In 2019, Facebook faced a significant breach due to a BOLA vulnerability in its API. According to API Security.io, attackers exploited this flaw by manipulating object IDs in API requests to access data they were not authorised to view. This vulnerability allowed unauthorised access to the personal information of millions of users, including phone numbers and private group membership data. The exploit bypassed insufficient access controls to retrieve sensitive information directly through API endpoints.
This breach underscores the critical need for robust object-level authorisation checks to ensure APIs validate user permissions for every request. Without such controls, APIs remain vulnerable to attackers altering object identifiers to gain access to restricted data.
Addressing these security gaps can help organisations mitigate risks associated with BOLA and protect sensitive data from unauthorised access.
The Optus Leak (2022)
In September 2022, Optus suffered a major data breach that released the personal details of 9.8 million individuals. The leak stemmed from vulnerabilities in its API security. The breach exposed personal information, including names, dates of birth, phone numbers, and identification numbers. Attackers exploited an unauthenticated API endpoint, enabling access to sensitive customer data without authorisation.
This incident revealed critical security lapses, such as the absence of authentication mechanisms, insufficient rate limiting, and inadequate monitoring of API endpoints. It underscored the urgent need for robust API security practices, including implementing strict authentication protocols, enforcing comprehensive access controls, and employing continuous monitoring to detect and prevent unauthorised access attempts.
Conclusion
APIs are the backbone of modern digital ecosystems, which makes them a primary target for cyber threats. Securing APIs is not just about compliance; it is about building trust, protecting sensitive data, and ensuring operational continuity. Organisations can safeguard their digital infrastructure while enabling innovation and collaboration by adopting a comprehensive approach to API security—spanning design, development, deployment, and maintenance.
This guide highlights the proactive strategies required to protect these vital assets, from understanding the unique risks posed by APIs to implementing robust lifecycle security measures. Addressing vulnerabilities like BOLA, injection attacks, and rate-limiting issues ensures that organisations remain resilient in an evolving threat landscape. Incorporating secure coding practices, CI/CD integration, and continuous testing strengthens security at every stage of the API lifecycle, reducing the likelihood of breaches and service disruptions.
This continuous focus on security mitigates risks and reinforces the confidence of stakeholders and customers in a highly interconnected digital economy. Embracing these strategies is essential for Australian businesses to thrive securely in today’s competitive and rapidly evolving technological landscape.
Galah Cyber Can Strengthen the Future of Your Business
At Galah Cyber, we specialise in helping Australian businesses protect their APIs through tailored security strategies and expert support. Visit our AppSec as a Service page to learn how we can help you strengthen your API security.







