APIs are the backbone of modern applications, allowing different systems to communicate. However, if not adequately secured, they can also open doors for potential cyberattacks. In 2022, Optus’ internal network compromised personal information, impacting nearly 40% of the population (9 million customers). ITNews believes the cybercriminal group gained access by bypassing an API endpoint.
This guide aims to provide development teams across Australian businesses with an open toolbox, revealing the top API security tools and practices. Understanding and implementing these practices is crucial to protecting digital assets and maintaining customer trust, whether a small startup or a large enterprise.
What Are API Security Tools?
API security tools are specialised software solutions that protect APIs from threats and vulnerabilities. They provide various functionalities such as monitoring, threat detection, access management, and vulnerability scanning. These tools assist developers with many aspects of API security, reducing manual tasks and ensuring a consistent and comprehensive security posture across their entire API ecosystem.
Top API Security Tools
API security requires the right tools to protect against threats and ensure secure, smooth operations. Here are some of the best-suited solutions addressing API gateways, authentication, threat detection, and vulnerability management:
API Gateways
- Apigee (by Google Cloud): Known for robust API management capabilities, Apigee offers security features like OAuth integration, rate limiting, and data encryption. It’s ideal for enterprises looking for a full-stack API gateway solution with security.
- Kong Gateway: An open-source gateway that supports traffic management, authentication, and rate limiting. It is highly customisable and ideal for businesses seeking a flexible solution for securing APIs.
- AWS API Gateway: This service supports rate limiting, logging, authentication, and authorisation out of the box—ideal for organisations currently using the AWS ecosystem.
Identity and Access Management (IAM) Solutions
- Auth0: A versatile solution that supports OAuth 2.0, OpenID Connect, and multi-factor authentication, ensuring secure access control for APIs—ideal for businesses needing scalable and user-friendly authentication.
- Okta: Provides identity management and integrates with API gateways for secure user authentication and role-based access control—ideal for enterprises seeking a centralised identity solution.
- Ping Identity: Specialises in API security through token management, OAuth, and OpenID Connect—ideal for businesses that require robust user identity and access management for their API ecosystem.
API Security and Threat Detection Tools
- Salt Security: As the leading platform in API security, Salt Security utilises AI and machine learning to dynamically detect and prevent API attacks by continuously monitoring API traffic for anomalies and identifying blind spots and potential risks.
- 42Crunch: This API security company offers automated API security testing, risk scoring, and compliance checking to secure APIs for enterprises from development through deployment.
- Traceable AI: Continuously monitors API traffic for anomalies and identifies potential abuse to provide actionable insights via AI—ideal for organisations seeking deep visibility into APIs to improve their API security posture.
Web Application Firewalls (WAF) for API Protection
- Akamai Kona Site Defender: A WAF that protects against web and API attacks, including DDoS mitigation—ideal for businesses that require global reach and robust protection for their APIs.
- Imperva API Security: Offers a WAF specifically tailored for APIs, providing deep packet inspection, DDoS protection, and automated API discovery—ideal for enterprises that need advanced protection against a wide range of API threats.
- Cloudflare API Shield: Provides mTLS (mutual TLS), DDoS protection, and schema validation for APIs—ideal for businesses looking to secure their APIs with a user-friendly interface and integration options.
Vulnerability Scanning and API Testing Tools
- Burp Suite (PortSwigger): A widely used tool for penetration testing and security analysis of APIs—ideal for security professionals looking to test API security rigorously and identify potential vulnerabilities.
- OWASP ZAP (Zed Attack Proxy): An open-source security tool that scans APIs for security flaws, such as injection vulnerabilities and configuration issues—ideal for development teams seeking a free and community-supported option.
- Postman: While known as an API development and testing tool, Postman also offers security testing capabilities, such as simulating various types of API requests and analysing responses for vulnerabilities.
Comprehensive API Security Platforms
- Data Theorem: Automates API security scanning and provides continuous monitoring, which is ideal for businesses looking for end-to-end protection for mobile apps and APIs—ideal for identifying misconfigurations and security gaps.
- RapidAPI: Offers API management with security monitoring and analytics—ideal for businesses that need visibility into their API performance and potential security issues in real-time.
- Tyk: An API gateway with robust security features like rate limiting, access control, and API analytics—ideal for businesses seeking a solution that combines API management with built-in security capabilities.
Security Information and Event Management (SIEM) for APIs
- Splunk: A leading SIEM solution that integrates well with API logging and monitoring, providing real-time analysis and alerts for security incidents—ideal for businesses needing detailed insights into API traffic and potential security threats.
- Elastic Security (formerly ELK Stack): Offers powerful logging and monitoring capabilities for APIs—ideal for businesses looking for a flexible, open-source solution for analysing API logs and detecting anomalies.
- IBM QRadar: A SIEM platform that provides real-time threat detection and analysis for API traffic—ideal for larger enterprises looking to integrate API security into their broader security operations.
These are feature-rich suites of options for traffic management, user authentication, and threat and vulnerability detection in API security. Whether the requirement is business monitoring, identity management, or advanced protection of APIs, these tools will go a long way in securing APIs resistant to new emerging threats.

API Security Best Practices
- Rate Limiting and Throttling: Rate limiting and throttling are critical practices to safeguard APIs from excessive requests. By controlling the requests a user or application can make, businesses can protect their infrastructure from DDoS attacks. Throttling also prevents API abuse, ensuring fair usage among all users. Tools such as AWS API Gateway and Apigee offer robust solutions to manage these controls effectively.
- Continuous Monitoring and Logging: Monitoring API usage and maintaining logs are crucial to detecting potential security breaches. Logging enables information on API interaction and how it is used and captures any abnormal behaviours indicative of an attack. To address any threat quickly, it is ideal to use systems that have the capabilities of real-time monitoring and alarms. Logging should be designed to catch critical information while ensuring privacy and other relevant requirements are not breached.
- Secure Data Transmission with Encryption: Data loss can be prevented through protective measures such as information encryption over APIs. The TLS should be extended to all API passages. The data in motion would be encrypted so that no unauthorised third party would get access to the information and any type of tamper-proofing. All businesses should update their encryption methodologies with the ever-evolving standards on time to keep them secure.
- Regular Security Audits and Penetration Testing: Security audits and penetration testing will help find those vulnerabilities within the API infrastructure. It provides you a clear view of the potential weaknesses that automatic testing tools might not discover. Let cybersecurity experts perform these tests, and you will have thorough scrutiny of your API security measures and go through with actionable insight into strengthening your defences.
- Embrace the Zero Trust Model for API Security: The Zero Trust security model is gaining traction as a robust approach to API security. It assumes that every internal or external request could be a potential threat. This approach involves verifying every request’s identity and intent before granting access, ensuring that even if attackers bypass the perimeter, they cannot exploit internal APIs.
In 2002, Optus’ internal network compromised personal information, impacting nearly 40% of the Australian population
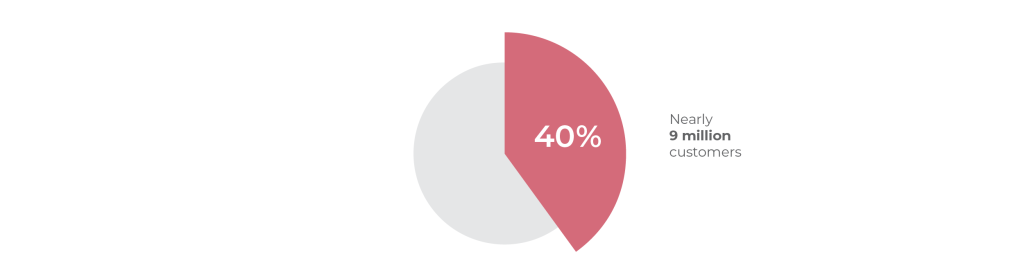
The cybercriminal group is believed to have gained access through an unauthorised API endpoint.
source: ITNews
Why Businesses Should Leverage API Security Tools
- Automated Threat Detection and Response: API security tools provide automated monitoring and threat detection. This proactive approach minimises the risk of breaches and ensures that security measures keep up with evolving threats.
- Enhanced Access Control and Data Protection: Tools like API gateways and IAM solutions provide granular control over who can access APIs and what data they can retrieve. This ensures that sensitive information is restricted only to authorised users.
- Compliance and Regulatory Adherence: API security tools help businesses comply with strict regulatory requirements for data protection by ensuring that data is securely transmitted, stored, and accessed in accordance with legal standards.
- Scalability and Flexibility: API security tools provide scalability, allowing organisations to easily manage and protect thousands of APIs without a proportional increase in manual effort.
- Improved Business Continuity: Leveraging robust API security tools allows businesses to reduce the likelihood of successful attacks and maintain uninterrupted operations, ultimately protecting their revenue and brand reputation.

Conclusion
Protecting APIs is a critical component of any cybersecurity strategy. Australian companies can significantly enhance their API security posture by adopting the abovementioned practices and tools. Apigee, AWS API Gateway, and Auth0 provide essential traffic management and secure authentication, while solutions like Salt Security, 42Crunch, and Akamai Kona Site Defender offer real-time protection against threats and attacks. By adopting the right tools for the job and fostering a culture of good practices, businesses can achieve an integrated approach to security and strengthen their relationships with their customers.
The importance of investing in good API security cannot be overstated, especially in a landscape where the cost of a breach can be substantial—not just in terms of finances, reputation, and trust. These measures mitigate these risks and safeguard customer trust for a better commercial outcome.
Galah Cyber Helps Tighten Your Security
Securing your APIs is a continuous journey, not a one-time task. At Galah Cyber, we specialise in helping Australian businesses build robust API security frameworks tailored to their unique needs. Our team provides expert guidance on everything from implementing best-in-class security tools to continuous monitoring and threat response. Visit our Application Security as a Service page to learn more about how we can help you protect your APIs and digital assets.







